Findings and Challenges
The majority of organizations, both public and private, are now facing growing complexity in cybersecurity :
• Cyberattacks affect both the most critical entities and smaller organizations
• This exposure is even more difficult to manage for structures with limited resources or processes that are still poorly formalized
• Regulatory and contractual requirements in cybersecurity are increasing, and their follow-up is becoming more restrictive
• Cybersecurity is now a key criterion in evaluating and referencing suppliers
Main Challenges
You need to devote your time to what really matters for your business, and cybersecurity is not your core activity. Taking cybersecurity into account presents many challenges :
Managing to hire or mobilize an internal cybersecurity resource
→ Rare skill, low availability, limited budget
Finding an outsourced cybersecurity support offer that fits your context
→ Maturity and price often very high for this type of structure
Choosing a trusted, responsive contact person
→ Large consulting firms generally prioritize large account clients
Capitalizing on your cybersecurity investments
→ Strong dependence on the consultant and Excel files
Our Mission
Make cybersecurity a real growth lever by:
✔ Significantly reducing your risks of compromise and business interruption
✔ Capitalizing on your compliance initiatives and gaining easier access to certifications
✔ Meeting your partners’ expectations by opening new market opportunities
Our Approach
A tailor-made support offer, adapted to the context and challenges of each client, which relies on a 4-step approach :
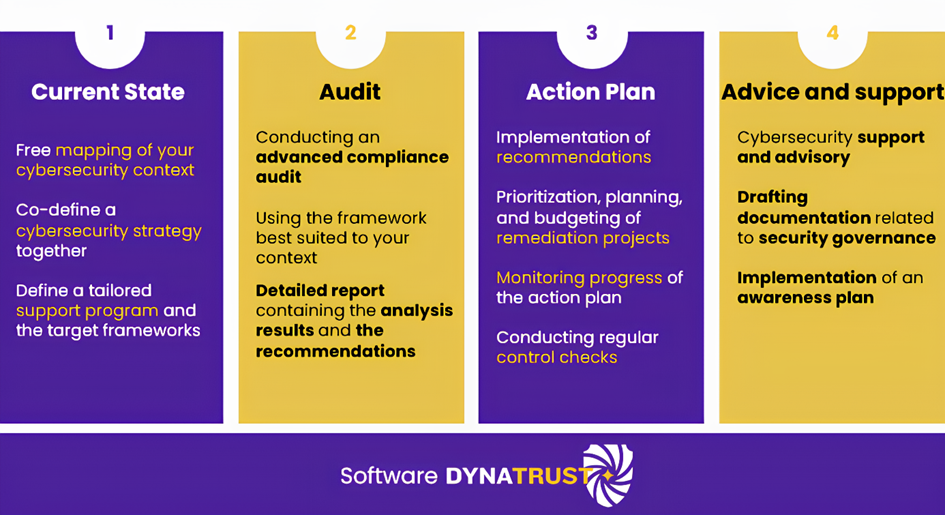
Why work with us ?
We offer a combined offer combining the proximity and expertise of a certified consultant with the innovation and efficiency brought by a dedicated software :
- GRC Expert
Our cybersecurity experts are PECB certified (ISO/IEC 27001, ISO 27005). They offer you close support, responsive and personalized with the objective of helping you gain cybersecurity maturity and become autonomous in the long run.
- DYNATRUST Platform
Developed by our teams to manage your compliance implementation and that of your partners, this software, 100% sovereign and AI-powered, allows among other things to perform multi-framework mapping and to capitalize on your achievements.
Example of a Client Case
We supported an organization in the digital services sector whose objective was to reassure its current clients and major partners about its level of cybersecurity maturity.
The objective over 2 years was to achieve ISO/IEC 27001:2022 certification.
Its main challenge was not only technical, but organizational: lack of governance, heterogeneous practices, little traceability and a significant workload related to monitoring actions.
We first defined a realistic and iterative strategy together. Given the initial maturity level, we recommended implementing the ANSSI hygiene guide as a first milestone. We then established the methodological framework.
The software platform allowed us to centralize all evidence, actions, audits and requirements in order to have real-time monitoring. Thanks to multi-framework mapping, we immediately projected ourselves towards the final certification objective.
During the first year, we :
- Carried out an initial audit with respect to this framework
- Built the prioritized action plan
- Managed the action plan and implemented the security measures directly linked to GRC.
During the second year, we focused on ISO/IEC 27001:2022 by capitalizing on everything that was achieved during the first year of intervention. An internal audit in accordance with ISO 19011 was carried out via the platform. We then formally prepared our client for certification.
Result : Our client not only obtained their certification, but also significantly strengthened their cybersecurity maturity by establishing a clear, sustainable governance operated in a single tool, which would not have been possible with a purely “consultant” or purely “software” approach.
Why is this approach differentiating ?
Because it:
- avoids dependence on the consultant and makes teams autonomous
- greatly reduces administrative workload (evidence, audits, reporting)
- guarantees continuous and no longer occasional traceability
- allows capitalizing on and reusing the work already done
- truly aligns practices between teams (IT, projects, business, management)
If you wish to benefit from the same level of support, personalized and adapted to your situation, feel free to contact us. Our consultants can help you turn your cybersecurity into an opportunity ! 🤝

